
Phishing. What is it, and how do I avoid becoming a victim?
Phishing is a form of social engineering that tricks users into giving away sensitive information (for instance, user names or passwords) by masquerading as a trusted source. For example, a phisher will email a potential victim pretending to be their bank and ask for their bank account credentials. After you have read this article you should know what phishing is, how to spot it and how to avoid becoming a victim.
Within the phishing family of social engineering tricks there are some variants which you should also be aware of. These include:
- Pharming
An attack on network infrastructure where a user is redirected to an illegitimate website, despite having entered the right address, creating a man-in-the-middle attack. - Smishing
Phishing via SMS: mass text messages sent to users asking for sensitive information (eg bank details) or encouraging them to visit a fake website. - Spear Phishing
Spear phishing is a cyber attack that aims to extract sensitive data from a victim using a very specific and personalised message designed to look like it’s from a person the recipient knows and/or trusts. - Whaling
Highly targeted phishing attacks (masquerading as a legitimate emails) that are aimed at senior executives.
How do I spot phishing?
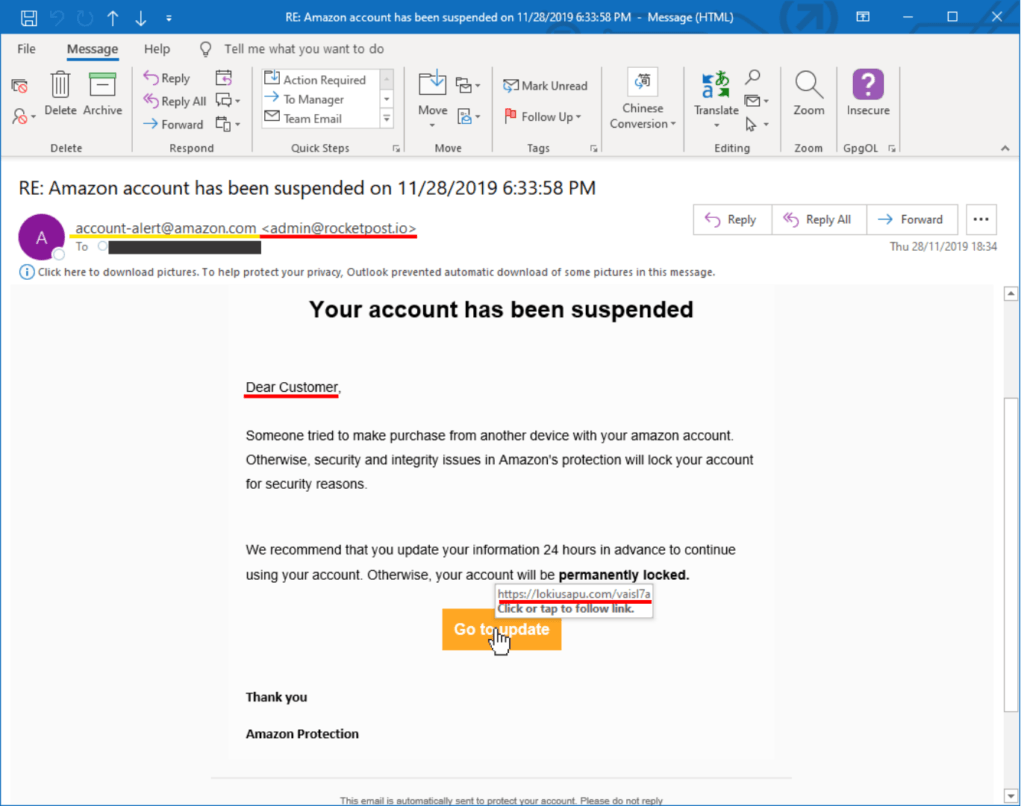
Here is an example of a phishing email sent to me. I have highlighted some important features you should look out for on every email you receive.
The yellow underlined “from” address of “account-alert@amazon.com” doesn’t match the red underlined actual from email address of “<admin@rocketpost.io>”.
The salutation of “Dear Customer,” is too generic. An email from a company you have a relationship will typically use your name.
Grammar is incorrect. They even failed to capitalise Amazon in the first sentence.
The link (which Outlook shows you as a pop-up) isn’t what you would expect from Amazon.
The grammatical structure of the email is wrong, and it appears that the bottom paragraph and [Go to update] button should be before the threatening second sentence.
All these red flags are telling you that this is a phishing email.
Below is another new example of a phishing email we found recently, it’s biggest flaw is that the sender obviously has no idea how webmail works. Webmail never needs to be “upgraded” unless you are the system administrator of a server hosting a webmail service.
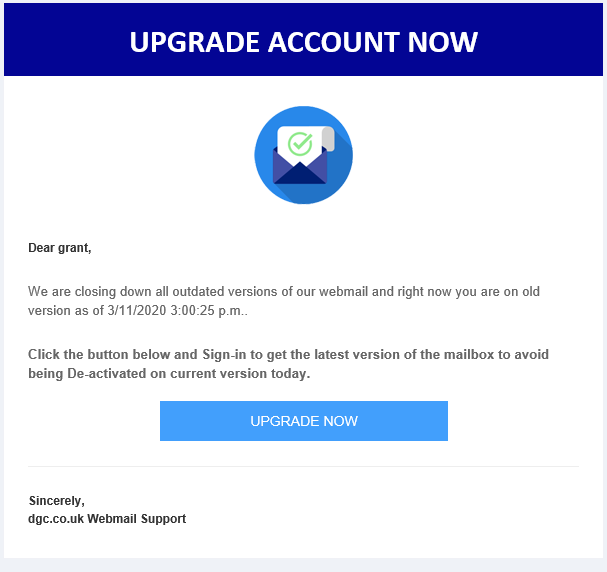
The link attached to the “UPGRADE NOW” button is bogus and there is no capitalisation on the recipient’s name and I don’t know of any webmail service provider that would call themselves by their fully qualified domain name.
The grammar is also wrong in the first paragraph, with no punctuation. The second paragraph grammar is also wrong.
It’s these simple clues that make this phishing email stand out like a sore thumb.
Compare and contrast
Below I have two example emails apparently from “TV LICENSING”, one is real and one is totally bogus. It’s really easy to see which is which. Firstly the real one contains information that wouldn’t normally be available to a cyber-criminal (but could be).
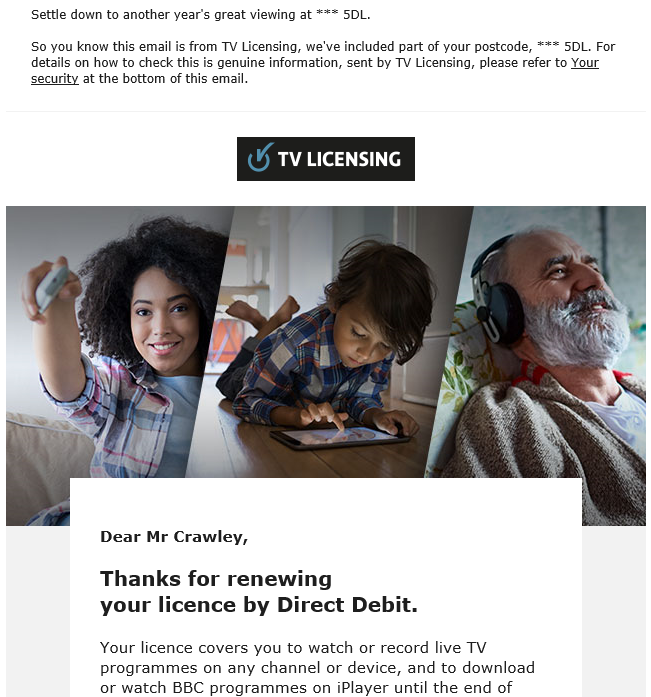

The image on the left is genuine, it’s for my annual TV Licence renewal, the one on the right is the Phishing email. I captured the screen with the pop-up link for the button, so you can see where it directs to. The bogus mail uses a link shortener to take you to a phishing site to get your debit card details and bank details. It uses my email address as the salutation, which no business would ever do. The TV licence number is wrong, it’s just made up.
However, this is a pretty good attempt, and will fool a lot of people. Who’s going to go and get their TV licence to check it’s number, or check their bank account. The logo is correct(ish) and the colours are right for older TV Licensing emails.
How do I avoid becoming a victim?
Firstly, you need to change your mindset from being trusting, to a default position of distrust. Especially when it comes to email and text messages. I know that’s easier said, than done.
Changing your mindset aside, here are some easy to implement tips to help you avoid becoming a victim of a phishing attack.
- Never, ever, ever… click a link in an email to any website requiring a login. So that’s everywhere: banks, eBay, Amazon, shopping sites… everywhere.
- Always, without fail… type in the link of where you want to go into the address bar of your browser, or use your own bookmarks. Do not rely on search engines.
- Always, without fail… check the certificate attached to the browser padlock icon is valid and issued to the site you are visiting.
- Always, without fail… check that the from address and links in emails match the organisation you expect them to be… But still NEVER CLICK THEM.
- If a friend or colleague is asking you to help them, then pick up the phone and call them to confirm.
- Read email messages, if they look iffy then they probably are. Amazon is not going to have grammatical errors in a standard message.
- Whenever possible, enable two-factor authentication on important accounts. Either by text message or using an authenticator app such as Google Authenticator or Symantec VIP.
- Use unique passwords for all of your accounts. We recommend a free tool called KeePass to manage your passwords (it will even generate secure ones for you too).
What about the phishing variants?
The tips above apply equally to other variants of phishing. So you should certainly implement them straight away.
Pharming
Probably the hardest to identify, Pharming is an attack on your network infrastructure. It then creates fake versions of the websites the hacker wants capture credentials for, the way to check is to verify the certificate as in tip 3 above. You can enhance your success rate by cross-checking the signature on a different network, such as your mobile phone. Just make sure it’s on mobile data and not the same network as your PC (turn off WiFi).
Smishing
Rarely will a legitimate company or contact send you a link in a text or SMS message, so bear that in mind and never click any. If you get a notification from your bank or PayPal or any other sensitive account, connect to them using your normal mechanism. Do not click any link in a text message, and do not engage with the text message sender.
Spear Phishing
These attacks are highly targeted, they will often appear to come from a trusted source, such as a friend or a company you deal with regularly. Be suspicious, if you’re not expecting something then chances are it’s not legitimate. Much better to pick up the phone, or message them using a different media (WhatsApp, Skype, Messenger etc) to ask them to confirm the legitimacy of what you’ve received.
Whaling
Essentially the same as Spear Phishing, but targeted at senior executives. The same countermeasures apply.
Get Virtco Threat Report
[pt_view id=”1e954a46xk”]